OPTIMIZED GENETIC ALGORITHM AND EXTENDED DIFFIE HELLMAN AS AN EFFECTUAL APPROACH FOR DOS-ATTACK DETECTION IN CLOUD
DOI:
https://doi.org/10.15282/ijsecs.8.1.2022.7.0097Keywords:
Genetic Algorithm, Extended Deffie hellman Algorithm, Encryption time, Decryption time, Cloud Computing, Intruders, Intrusion detection, Middle-man attack, Denial of sevicesAbstract
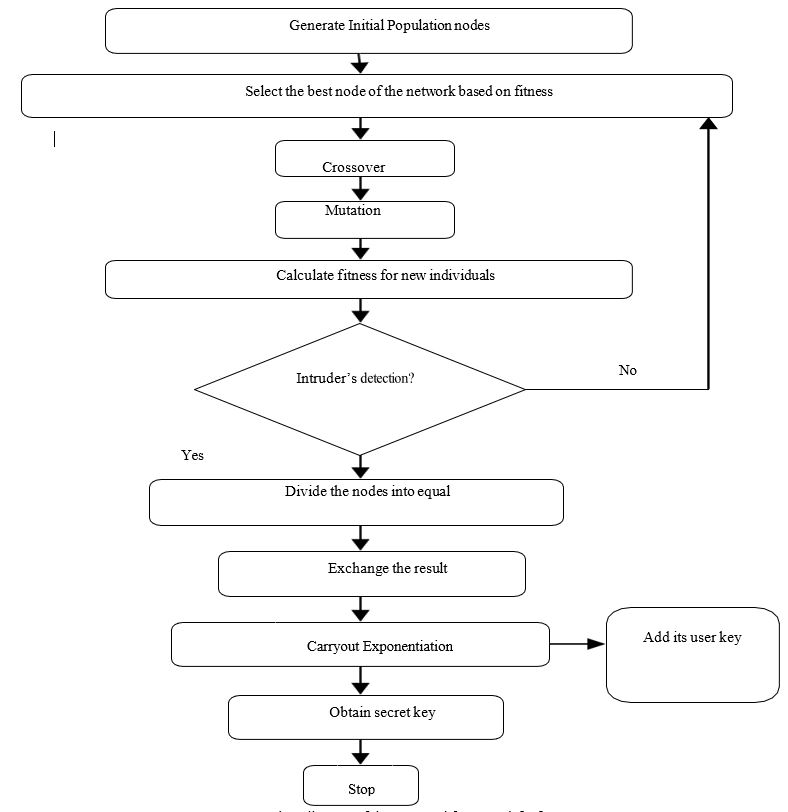
Cloud computing is a mode to increase competence and capabilities devoid of investing in any infrastructure. It seems that in cloud computing environment the major problem that ensure the secure communication and protect responsive data in open networks from unauthorised access. These days it seems the headlines are jam-packed with stories about security breaches to these services; that result in the leak of a large amount of private data of the users. As cloud computing can offer new computing benefits, but it faces soaring risks, specifically on the security side where DOS attacks can make cloud services unavailable. This paper aims to turn up an effective method of detecting DOS attacks with an optimized Genetic algorithm and extended version of Diffie-hellman algorithm. To prevent data loss or corruption caused by the insiders in the cloud, Optimized Genetic Algorithm (OGA) is utilized, which effectively recovers the data and retrieve it if the missed data without loss. It is then followed with the decryption process as if requested by the user. An optimized path assortment for information broadcast proves to be an effective method in the cloud computing atmosphere. The proposed framework ensures certification and paves way for secure data access in an unauthorized network, with improved performance. It successfully assure the high level of protection of the transmission and data transmitted. And concurrently reduce the communication complexities.To reduce time complexity and detect the attackers by mutual secret key that is brought on using extended version of Diffie-hellman to endorse available key generation.
References
A. T. H. Ibrahim, Ibaryaqoob, N. B. Anuar, S. Mokhtar, A. Gani and S. U. Khan, “The rise of ‘Big Data’ on cloud computing,”
Elsevier publication, pp. 98-115, 2015, DOI:10.1016/j.is.2014.07.006.
A. Giuseppe, B. Alessio, D. Walter, P. Antonio, “Survey cloud monitoring: a survey,” Computer Network, pp. 2093-2115,
, DOI:10.1016/j.jpdc.2014.06.007.
T. Gunarathne, B. Zhang, T. ~L. Wu and J. Qiu, “Scalable parallel computing on cloud using twister azure iterative
mapreduce,” Future Journal Computer System, pp. 1035-1048, 2013, doi: https://doi.org/10.1016/j.future.2012.05.027.
C. Te-Shun, “Security threats on cloud computing vulnerabilities,” International Journal of Computer Science & Information
Technology (IJCSIT), Vol. 5, No. 3, June 2013, DOI:10.5121/ijcsit.2013.5306.
D. Catteddu and G. Hogben, “Cloud computing benefits, risks and recommendations for information security,” The European
Network and Information Security Agency (ENISA), November 2009, DOI:10.1007/978-3-642-16120-9_9.
L. Kangchan, “Security threats in cloud computing environment,” International Journal of Security and its Applications, Vol.
, No. 4, October 2012,
M. N Ismail, A. Aborujilah, S. Musa and A. Shahzad, “New framework to detect and prevent denial of service attack in
cloud computing environment,” International Journal of Computer Science and Security (IJCSS), Vol. 6, Issue 4, doi:
http://dx.doi.org/10.15520/ajcsit.v4i12.12.
S. Ather, C. Sarah, G. Shengqi, V. Drew, “Current security threats and prevention measures relating to cloud services, hadoop
concurrent processing, and big data,” IEEE 2015.
C. Deyan and Z. Hong, “Data security and privacy protection issues in cloud computing,” International Conference on
Computer Science and Electronics Engineering, 2012, DOI: 10.1109/BigData.2015.7363960.
K. M. Tanzim, A B M Shawkat Ali and Saleh A. Wasimi, “Classifying different denial-of-service attacks in cloud computing
rule-based learning,” Security and Communication Networks in Wiley online Library, Vol. 5, pp. 1235-1247, September
, DOI:10.1002/sec.621.
M. T. Khorshed., “A survey on gaps, threat remediations challenges and some more thoughts on proactive attacks detection
in cloud computing,” Future Generation Computer Systems 2012, DOI:10.1016/j.future.2012.01.006.
S. Tanya, V. Seema, K. Vartika and K. Sumeet, “Intrusion detection system using genetic algorithm for cloud,” ACM, March
, DOI:10.1145/2905055.2905175.
A. Umar, N. Shahid, A. Fahad, A. Tahir and A. K. Wasim, “Intrusion detection and prevention in cloud computing using
genetic algorithm,” International Journal of Scientific & Engineering Research, vol-5, December 2014, doi:
https://doi.org/10.1145/2905055.2905175
A. G. Shivani and H. P. Manjunath, “Extension of diffie hellman algorithm for multiple participants,” IJIREEICE, vol-3,
April 2015.
S. Subashini and V. Kavitha, “A survey on security issues in service delivery models of cloud computing,” Journal of
Network and Computer Applications, Vol. 34, pp. 1-11, 2011, doi: https://doi.org/10.1016/j.jnca.2010.07.006.
H. R. Frederick, “Adaptation in natural and artificial systems by john h. holland,” University of Michigan Press, Ann Arbor,
vol-18 issue-3, July 1976, DOI:10.1137/1018105.
W. Diffie and M. Hellman, “New directions in cryptography,” IEEE transactions on information theory, vol-22, pp. 644-
, November 1976, DOI:10.1109/TIT.1976.1055638.
M. Steiner, G. Tsudik, M. Waidner, “Diffie hellman key distribution extended to groups,” Conf. computer and
communication security, pp. 31-37, 1996, doi: https://doi.org/10.1145/238168.238182.
G.P. Biswas, "Diffie hellman technique: extended to multiple two-party keys and one multi-party key," IET Information
Security, vol-2, pp. 12-18, September 2006, DOI:10.1049/iet-ifs:20060142.
S. Jerald Nirmal Kumar, S. RavimaranandM. M. GowthulAlam, “An effective non-commutative encryption approach with
optimized genetic algorithm for ensuring data protection in cloud computing,” CMES, 2020,
DOI:10.32604/cmes.2020.09361.
C. Himanshi, A.K. Sharma, “Hybrid technique of genetic algorithm and extended diffie hellman algorithm used for intrusion
detection in cloud,” ICEEE, 2020, DOI: 10.1109/ICE348803.2020.9122978
C. M. Dan, K. Morgan, “Cloud Computing Theory and Practice,” books.google.com, 2017.
Downloads
Published
Issue
Section
License
Copyright (c) 2022 Himanshi Chaudhary, Himanshu Chaudhary, Awadhesh Kumar Sharma

This work is licensed under a Creative Commons Attribution-NonCommercial 4.0 International License.






