SECRS TEMPLATE TO AID NOVICE DEVELOPERS IN SECURITY REQUIREMENTS IDENTIFICATION AND DOCUMENTATION
DOI:
https://doi.org/10.15282/ijsecs.8.1.2022.5.0095Keywords:
security requirements, security requirements engineering methods, SQUARE, CLASP, Usability, ApplicabilityAbstract
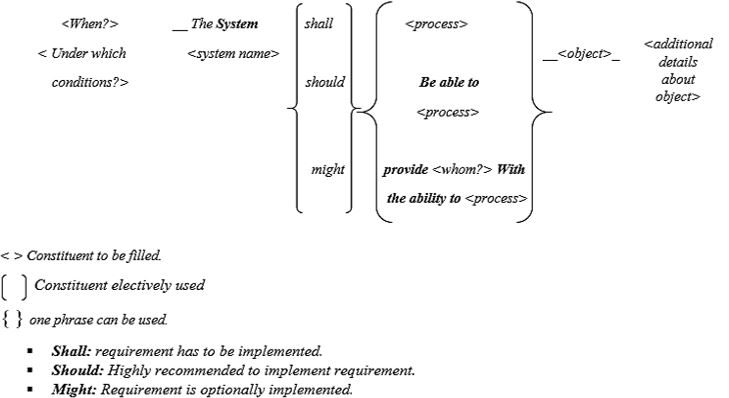
The security requirements are one of the non-functional requirements (NFR) which acts as a constraint on the functions of the system to be built. Security requirements are important and may affect the entire quality of the system. Unfortunately, many organizations do not pay much attention to it. The security problems should be focused on the early phases of the development process i.e. in the requirements phase to stop the problems spreading down in the later phases and in turn to avoid the rework. Subsequently, when security requirements are to be focused, proper guidance should be provided which should assist requirements engineers. Many security requirements engineering methods were developed in the past which require different level of expertise such as SQUARE process which requires requirements engineer to have a certain level of security expertise. Moreover, it lacks proper guidance especially for novice developers in applying the existing security requirements engineering (SecRE) methods to identify security requirements. Hence, this study intends to address the gap by developing a guided template to assist novice developers in the security requirements identification and documentation. The main objectives of the research are: 1) to study and investigate the existing security requirements engineering (SecRE) methods. 2) To develop a template to aid novice developers in identifying and documenting security requirements. The developed template is applied to two case studies of software projects to determine its usability and applicability. The results of the case studies evaluation show that both the usability and applicability of the template is good. The template is also evaluated by several experts and software practitioners. The evaluation results show that the SecRS template is found to be satisfying the usability and applicability factors; thereby confirming that the proposed template achieves its desired objective of aiding the novice developers to identify and document security requirements correctly.
References
Mouratidis H, Giorgini P. Secure tropos: a security-oriented extension of the tropos methodology. International Journal of Software Engineering and Knowledge Engineering 2007.
Jaffe M, Leveson N, Heimdahl M, Melhart B. Software Requirements Analysis for Real-Time Process-Control Systems. IEEE Transactions on Software Engineering 1991, Vol.17, No.3.
Haley C, Laney R, Moffett J, Nuseibeh B. Security Requirements Engineering: A Framework for Representation and Analysis. IEEE Transactions on Software Engineering 2008, Vol. 34, No. 1.
Hadary H, Kassas S. Capturing security requirements for software systems. Journal of Advanced Research 2014, Cairo University.
Ramesh MRR, Reddy DrCS. A survey on security requirements elicitation methods: classification, merits, and demerits. International Journal of Applied Engineering Research 2016. Volume 11, Number 1, pg. 64-70.
Firesmith D. Engineering Security Requirements. Journal of Object Technology 2003, Vol. 2, No.1, pg. 53-68.
Salini P, Kanmani S. A Survey on Security Requirements Engineering. International Journal of Reviews and Computing 2011. Vol.8.
Houmb SH, Islam S, Knauss E, Jurjens J, Schneider K. Eliciting security requirements and tracing them to design integration of Common Criteria, heuristics, and UMLSec. Special Issue – Security Requirements Engineering.
Requirements Engineering 2010, pg. 63-93.
Salini P, Kanmani S. Survey, and analysis on Security Requirements Engineering. Computers and Electrical Engineering 2012, Vol. 38, Issue.6, pg. 1785–1797.
Fabian B, Gurses S, Heisel M, Santen T, Schmidt H. A comparison of security requirements engineering methods. Special Issue – Security Requirements Engineering. Requirements Engineering 2010, pg. 7-40.
Mellado D, Blanco C, Sanchez L, Medina E. A systematic review of security requirements engineering. Computer Standards & Interfaces 2010. Vol. 32, Issue.4, pg. 153–165.
Hull E, Jackson K, Dick J. Requirements Engineering. Springer Books, 2011.
The CLASP Application Security Process. Secure Software, Inc. Book in 2005.
Mead N, Hough E, Stehney T. Security Quality Requirements Engineering (SQUARE) Methodology. Software Engineering Institute, Carnegie Mellon University. Technical Report CMU/SEI-2005-TR-009, November 2005.
Pohl K. Requirements Engineering: fundamentals, principles, and techniques. Springer Publishing Company, Incorporated in 2010. Conference proceedings.
Crook R, Ince D, Lin L, Nuseibeh B. Security Requirements Engineering: When Anti-Requirements Hit the Fan. In: IEEE 2002 Joint International Conference on Requirements Engineering (RE’02); 9-13 September 2002; Essen,
Germany. IEEE. pg. 203-205.
TKhilji WA. Evaluation Framework for Software Security Requirements Engineering Tools. Master’s Thesis (30 ECTS). Faculty of Mathematics and Computer Science, University of Tartu, 2014.
Salini, P., & Kanmani, S. A novel method: Ontology-based security requirements engineering framework. In Emerging Trends in Engineering, Technology, and Science (ICETETS), International Conference on (pp. 1-5).
IEEE.
Yahya, S., Kamalrudin, M., & Sidek, S. A review on tool supports for security requirements engineering. In Open Systems (ICOS), 2013 IEEE Conference on (pp. 190-194). IEEE.
Khan, N. F., & Ikram, N. Security Requirements Engineering: A Systematic Mapping (2010-2015). In Software Security and Assurance (ICSSA), 2016 International Conference on (pp. 31-36). IEEE.
Marquez, G., Silva, P., Noel, R., Matalonga, S., & Astudillo, H. Identifying emerging security concepts using software artifacts through an experimental case. In Chilean Computer Science Society (SCCC), 2015 34th
International Conference of the (pp. 1-6). IEEE.
Massacci, F., & Paci, F. How to select a security requirements method? A comparative study with students and practitioners. In Nordic Conference on Secure IT Systems (pp. 89-104), 2012. Springer Berlin Heidelberg.
Schmitt, C., & Liggesmeyer, P. Getting grip on security requirements elicitation by structuring and reusing security requirements sources. 2015, Complex Systems Informatics and Modeling Quarterly, (3), 15-34.
Anwar Mohammad, M.N., Nazir, M. & Mustafa, K. A Systematic Review and Analytical Evaluation of Security Requirements Engineering Approaches. Arab J Sci Eng 44, 8963–8987 (2019).
Khan, R. A., Khan, S. U., Ilyas, M., & Idris, M. Y. The State of the Art on Secure Software Engineering: A Systematic Mapping Study. 2020, Proceedings of the Evaluation and Assessment in Software Engineering, 487- 492.
Li, T., & Chen, Z. An ontology-based learning approach for automatically classifying security requirements. 2020, Journal of Systems and Software, 165, 110566.
Mufti, Yusuf, Mahmood Niazi, Mohammad Alshayeb, and Sajjad Mahmood. A readiness model for security requirements engineering. IEEE Access 6 (2018): 28611-28631.
Ansari, Md Tarique Jamal, Dhirendra Pandey, and Mamdouh Alenezi. STORE: security threat-oriented requirements engineering methodology. Journal of King Saud University-Computer and Information Sciences,
Downloads
Published
Issue
Section
License
Copyright (c) 2022 Nuzhat Qadir Tunio, Rodina Ahmad

This work is licensed under a Creative Commons Attribution-NonCommercial 4.0 International License.






