OPTIMAL RESOURCE SCHEDULING ALGORITHM FOR OFDMA-BASED MULTICAST TRAFFIC DELIVERY OVER WIMAX NETWORKS USING PARTICLE SWARM OPTIMIZATION
DOI:
https://doi.org/10.15282/ijsecs.7.2.2021.6.0089Keywords:
Simulated Kalman filter, Opposition-based learning, Current optimumAbstract
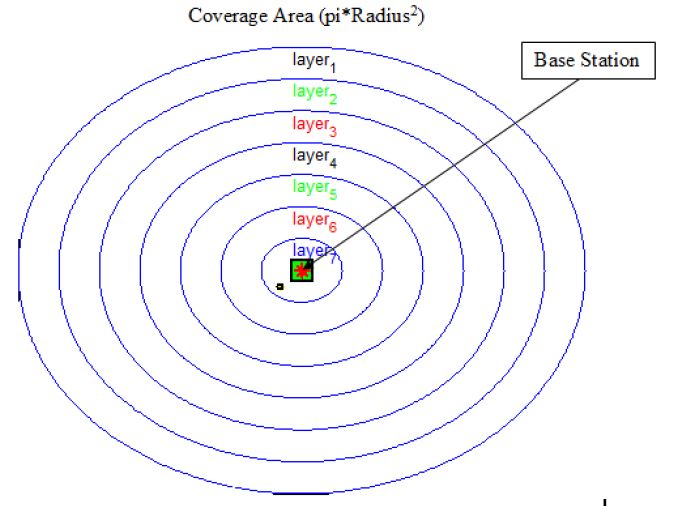
Researchers are yet to entirely mapped out the difficulty in allocating optimal resources to mobile Worldwide Interoperability for Microwave Access (WiMAX) subscribers. This research presents an optimal scheduling algorithm for WiMAX resource allocation based on an Particle Swarm Optimization (PSO). In this work, sub-group creation is used to offer a PSO-based technique for allocating subcarriers and Orthogonal Frequency Division Multiplexing (OFDM) symbols to mobile WiMAX customers. The WiMAX network environment is organized into seven layers, with seven different modulation and coding algorithms proposed for sending packets to subscribers within each layer. By adopting an improved PSO-based WiMAX resource allocation method, an enhanced model for throughput maximization and channel data rate was implemented. The Aggregate Data Rate (ADR) and Channel Data Rate (CDR) for each scenario were obtained by simulating several scenarios of WiMAX multicast service to mobile users. Based on the performance evaluation of the enhanced algorithm for ADR and CDR, the results for the various layers and uniform distribution of users over the full layers were 350Mbps, 525Mbps, 700Mbps, 1050Mbps, 1050Mbps, 1400Mbps, 1575Mbps, and 1398Mbps. 6.98Mbps, 10.48Mbps, 13.97Mbps, 20.95Mbps, 20.95Mbps, 27.94Mbps, 31.5Mbps, and 28Mbps were also achieved for CDR. The significance of optimal resource allocation is to achieved a maximum ADR and CDR. The results showed a fair distribution of resources within the coverage area of the network .
References
APWG (2020). Phishing Activity Trends Report for Q1 2020 retrieved from
https://docs.apwg.org/reports/apwg_trends_report_q1_2020.pdf
A. Alswailem, B. Alabdullah , N. Alrumayh, and A. Alsedrani (2019). Detecting phishing websites using machine learning.
In 2019 2nd International Conference on Computer Applications Information Security (ICCAIS), 1–6
Akshay Sushena Manjeri, Kaushik R., MNV Ajay, C. Nair Priyanka (2019). A Machine Learning Approach for Detecting
Malicious Websites using URL Features. 2019 3rd International Conference on Electronics, Communication and Aerospace
Technology (ICECA), 555–561. https://doi.org/10.1109/iceca.2019.8821879
A. M. Oyelakin , O. M. Alimi, Tosho Abdulrauf (2020). A Comparative Analysis of Machine Learning Algorithms for
Detecting Phishing Urls, Journal of Computer Science and Control Systems, Oredia University, Romania, 13(2):16-19,
available at https://electroinf.uoradea.ro/index.php/jcscs/12-cercetare/reviste/jcscs/213-1st-issue-vol-13-nr-2.html
M. A. Hall (1999). Correlation-based Feature Selection for Machine Learning, a PhD Thesis at University of Waikato
A. Chaudhary, S. Kolhe, & R. Kamal, (2016). An improved Random Forest Classifier for multi-class classification.
Information Processing in Agriculture, (September). https://doi.org/10.1016/j.inpa.2016.08.002
M. Zakariah (2014). Classification of large datasets using Random Forest Algorithm in various applications : Survey.
International Journal of Engineering and Innovative Technology (IJEIT), 4(3), 189–198.
E. Bauer and R. Kohavi (1999). An empirical comparison of voting classification algorithms: Bagging, boosting and variants.
Machine Learning, 36(1/2):525–536
L. Breiman (1996). Stacked regressions. Machine Learning, 24(1), 49–64.
Y. Freund & R. Schapire (1996). Experiments with a new boosting algorithm. In Proceedings of the Thirteenth International
Conference on Machine Learning, pp. 148–156 Bari, Italy.
Sagar Patil, Yogesh Shetye, Nilesh Shendage (2020).Detecting Phishing Websites Using Machine Learning, International
Research Journal of Engineering and Technology (IRJET),7(2)
V. Shahrivari, M. D. Muhammad and I. Muhammad (2020). Phishing Detection Using Machine Learning Techniques,
available at https://arxiv.org/pdf/2009.11116.pdf
D. Jampen, G. Gür, T. Sutter & B. Tellenbach (2020). Don ’ t click : towards an effective anti - phishing training . A
comparative literature review. In Human-centric Computing and Information Sciences. https://doi.org/10.1186/s13673-020-
-7
Rami Mohammad, T.L. McCluskey and Fadi Abdeljaber Thabtah (2014). Intelligent Rule based Phishing Websites
Classification. IET Information Security, 8 (3), 153-160. ISSN 1751-8709, available at
https://archive.ics.uci.edu/ml/machine-learning-databases/00327/
L. Breiman (2001). Random Forests, Machine Learning, 45(1), 5-32, 2001. Available at:
https://doi.org/10.1023/A:1010933404324
M. E. Fenner (2020). Machine Learning with Python for Everyone, Free Sample Chapter, Addison Wesley Data and
Analytics Series
Downloads
Published
Issue
Section
License
Copyright (c) 2021 Daniel Aliu, Muyideen Omuya Momoh

This work is licensed under a Creative Commons Attribution-NonCommercial 4.0 International License.






